
GitHub Repositories Actively Serving Malware
On March 9, security researcher JJ informed the GitHub Security Incident Response Team (SIRT) about a set of GitHub repositories actively serving malware. The malware was built to compromise NetBeans projects and all the affected projects were serving as backdoors without their owners knowing about it.
This malware, called the Octopus Scanner, lands on a machine and looks for the NetBeans IDE that is in use on a developer’s system. If it finds one, it ensures that each time a JAR is produced, it gets infected with a dropper. When executed, the payload spreads a Remote Access Trojan (RAT) connecting to C2 servers. The Octopus Scanner backdoors healthy projects so that when the code is released, it already contains the malware.
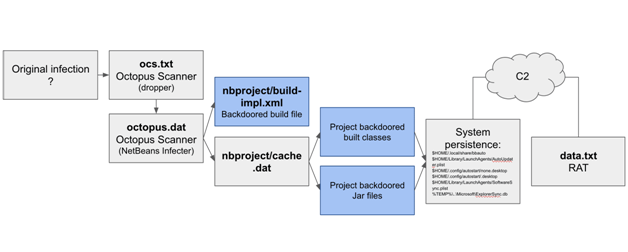
It should be noted that developers and several of the companies have turned their interests towards open source code in the recent past. Hence, Attackers too have begun to pursue supply chain attacks so as to have a widespread reach. “Infecting build artifacts is a means to infect more hosts since the infected project will most likely get built by other systems and the build artifacts will probably be loaded and executed on other systems as well,” explains the blog post. The blog further states that “a malware that abuses the build process and its resulting artifacts to spread is both interesting and concerning for multiple reasons.”









